SECURITY AND TRUST
Security is More Than Just a Task
It’s in the DNA of every employee, every product, and built into our culture. SoundThinking has defined how its systems and applications can be protected from new and emerging threats.
Certifications & Compliance Frameworks
It’s in the DNA of every employee, every product, and built into our culture. SoundThinking has defined how its systems and applications can be protected from new and emerging threats.













Cybersecurity Framework
Securing our hardware, software, data and AI use.
All US Customer solutions are hosted solely on infrastructure within in the United States. We do not directly use any Chinese company as a subprocessor, and to our knowledge none of our subprocessors do either.
We assign infrastructure access to team members on a least-privilege basis. We enforce multi-factor authentication for AWS. We restrict access to resources using both network-level controls and secrets.

Cybersecurity Framework
SoundThinking Security Policies
Robust and Comprehensive Security Program
- SoundThinking's Overall Information Security Policy – Board-approved and sets the tone for the organization's Information Security approach.
- Business Continuity, Disaster Recovery and Incident Response Policies and Plans – Details our responses to security events and incidents.
- Penetration Tests & Vulnerability Scans – SoundThinking maintains regular penetration scanning and vulnerability scans as part of its security program.
- All other policies include: Risk Assessment, Change Management, Credential Management, Patch Management, Data Classification, etc.
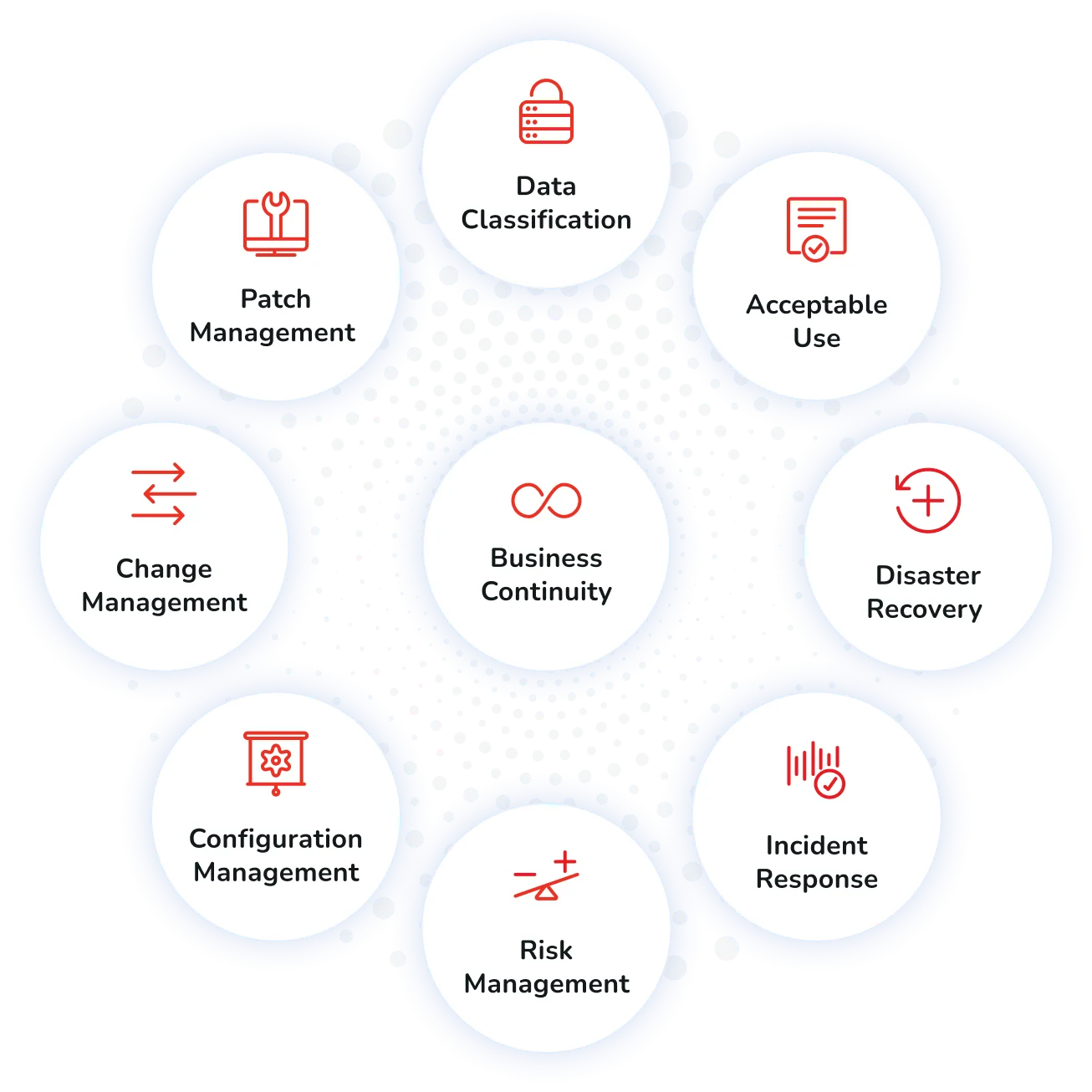
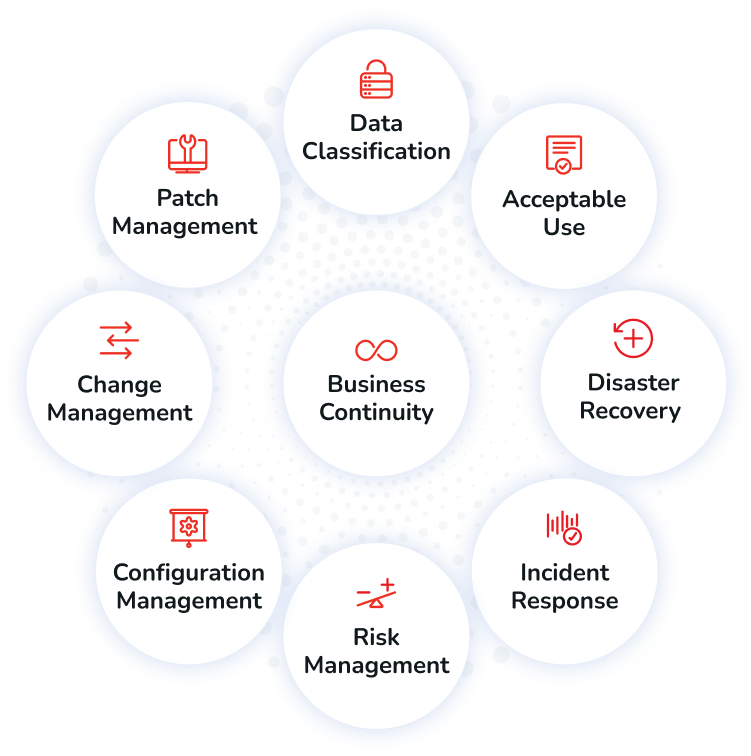
SoundThinking Security Policies
SoundThinkingAppSec Program
We integrate security into every stage of the Software Development Lifecycle, starting with secure design principals and validating security during the test and development cycle, prior to release.
Our commitment to transparency and trust means we embrace responsible disclosure and are transparent about material findings and evolving threats.
Key Security Practices
- Supply Chain Security – We vet dependencies, enforce SBOM requirements, and monitor for compromised packages.
- Vulnerability Management – We identify, prioritize, and remediate vulnerabilities with a risk-based approach.
- Security Validation – We validate security controls through internal and external Pen Testing, SAST, DAST, and manual assessment.
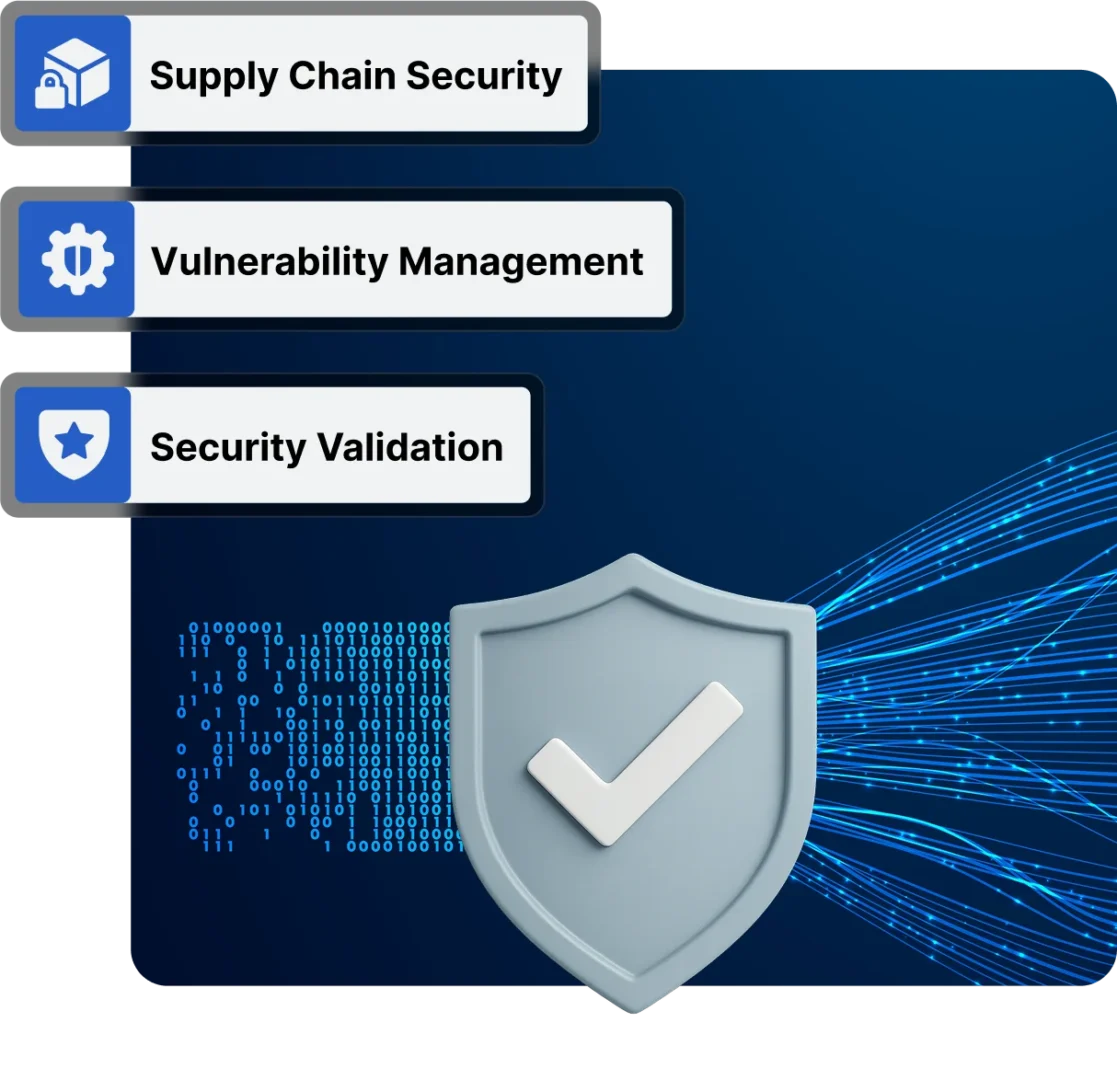
SoundThinking AppSec Program
Do you have any Questions?
Secure Hosting Platform
- Enhanced Security – The GovCloud region is built with specific security requirements in mind, such as the Department of Defense (DoD) SRG (Security Requirements Guide), Impact levels 4 & 5, FedRAMP high, and CJIS (Criminal Justice Information Services) for law enforcement data.
- Isolated Infrastructure – environments are physically and logically separate from commercial cloud regions, providing an additional layer of security and control.
- Designed for Sensitive Government Data & Workloads – GovCloud environments are specifically architected to host sensitive or mission-critical government applications.

Secure Hosting Platform
Artificial Intelligence Security
AI-Driven Threat Detection
Our AI-integrated security tools quickly identify, alert and/or neutralize potential threats, from phishing to ransomware.
Human Oversight and Accountability
AI outputs are always subject to human review, ensuring that decision-making aligns with ethical standards and regulatory compliance.
Privacy by Design
All personal data processed by AI systems is anonymized and protected, adhering to a zero-trust framework that limits access to only what is essential.
Artificial Intelligence Security
Compliance & Attestations
Together with Partners for Greater Public Safety
You can trust SoundThinking to handle your data securely. Our dedicated Compliance Program details our comprehensive security controls and our diligent adherence to all relevant Cybersecurity Laws, Regulations, Attestations, and Frameworks that are important to our customers.

SOC 2 is a cybersecurity compliance framework, developed by the American Institute of Certified Public Accountants (AICPA), designed to ensure service organizations securely manage customer data and systems. SoundThinking is aligned to Security, Availability, and Confidentiality Trust Services Categories.

SoundThinking provides assurances that we will comply with requirements for HIPAA Privacy, Security, and the HITECH Act.
SafePointe is the only SoundThinking Application in scope and undergoes HIPAA audits by a trusted third party auditor. For a copy of this attestation report, please contact a sales representative.

The California Consumer Privacy Act (CCPA) and the California Privacy Rights Act (CPRA) are laws that protect the personal information of California residents. The CPRA expanded on the CCPA and added new rights for consumers. Under the CCPA, consumers may request information about the personally identifiable information (PII), as well as the categories of PII a business collects and sells. The CPRA expands this right to include the data a business shares. It also expands the timeframe for which a consumer can request that information.
For more info: Privacy Page

The CSP (CJIS Security Policy) sets minimum security requirements for any authorized organization that wishes to access CJIS, or that processes and maintains criminal justice information (CJI).
Our products “CrimeTracer” and “CaseBuilder” endeavor to ensure that they remain compliant within the evolving CJIS security standard by the sanctionable and auditable dates within the policy.
We maintain security controls designed to meet CJIS Security Policy requirements. As no official FBI CJIS certification program exists, we demonstrate our commitment to compliance through independent third-party SOC 2 audits and stand ready to support your organization with detailed responses to CJIS-specific questionnaires and requirements.

TX-RAMP is a standardized framework for assessing and monitoring the security and risk of cloud-based services used by Texas state agencies, ensuring compliance with state cybersecurity requirements.

Adoption of policies, procedures, and security controls necessary to identify, protect, detect, respond, and recover from cybersecurity events. SoundThinking has its security program rooted in the NIST principles of SP 800-53 around safeguarding measures for all types of computing platforms, including general purpose computing systems, cyber-physical systems, cloud-based systems, mobile devices, Internet of Things (IoT) devices, and communications systems, among others. The objective is to make the information systems we depend on more penetration-resistant, limit the damage from attacks when they occur, make systems cyber-resilient and survivable and protect our data.
Robust Security & Privacy at SoundThinking
NextGen Security Tools
Automated Threat Detection
Our security tools quickly identify and neutralize potential threats, from phishing to ransomware and alert staff if further action is needed.
Encryption Standards
SoundThinking ensures its GovCloud-hosted CrimeTracer and CaseBuilder applications meet CJIS requirements via FIPS 140-2/3 standards. All data is secured using AES-256 (FIPS 197 compliant) at rest and TLS 1.2+ in transit.
Advanced Intrusion Detection
Edge systems include firewalls, anomaly detection and heuristic analysis to monitor for suspicious activity in real-time.
Multi-factor Authentication
SoundThinking supports two-factor authentication (2FA) in order to provide an additional layer of security to your account.
Data Retention Controls
SafePointe maintains HIPAA compliance to store the required records for a period of 6 years from the date of creation. Access to these records is based on least-privilege and need-to-know.
Internal Audits
The IT & InfoSec teams performs periodic audits to ensure ongoing compliance with our internal and external requirements and compliance audits.
Dedicated InfoSec Team
Security and IT Team maintain industry-best certifications including CISSP, and AWS Security Certifications among others.
Industry Partners
SoundThinking maintains partnerships with key vendors including but not limited to: AT&T Cybersecurity, Level Blue, CJIS Online, Qualys, Secure CyberDefence, & Palo Alto.
Incident Response Detection, Logging and Prevention
Through rigorous monitoring, logging and remediation, we have avoided all major incidents to date. Security logging to a centralized SIEM with retention of at least 365 days.
Key Security Practices



Security is Our Top Priority
Learn How We Can Help
Maximize impact through data-driven solutions
1
Connect with Our Team
A representative will reach out by email or phone to schedule a brief introductory call.
2
Discuss Your Needs
During this call, we’ll discuss the specific challenges faced by your agency and explore how we can help.
3
Personalized Solution
We will connect you with a solution architect who will provide a tailored demo and outline a clear roadmap.
Get In Touch Now
Find out more in a few easy steps and a representative will reach out by email or phone to schedule a brief introductory call.
"*" indicates required fields